Device Control
Secure, manage, and monitor USB and peripheral ports to prevent unauthorized data access and mitigate the risk of data theft or loss.
Trusted by organizations around the globe:

What is Device Control?
Device control means setting policies and measures to
oversee and manage the use of devices within an organization’s network or setting. It helps keep track of who can connect to them, what data they are able to access and what actions they are allowed to perform.
Device control plays a crucial role in mitigating insider risks
and protecting data within an company.
Discover how Safetica utilizes Device Control to manage insider risks and safeguard data.

Automatically scan, identify,
and classify connected
external devices used by
employees.

Set granular device control
policies and monitor all USB
ports and devices on all
endpoints.

Prevent and block
unauthorized device use.
Receive notifications and
reports regarding USB
activity on all endpoints.
Safetica enables easy management of a wide range of USB drive types, enhancing data security in diverse work settings.
- USB Storage Devices
USB Flash Drives,
Sticks, Pen drives,
etc.) - External HDDs (incl.
sATA HDDs) - CD/DVDPlayers and
Burners (internal and
external) - iPhones, iPads and
iPods - Smartphones and
Tablets (incl. Android
devices, Blackberry
and PDAs) - Digital Cameras
- MP3 Player and other
Media Player Devices
- Card Readers (internal
and external) - Memory Cards SD,
MMC, CF, Smartcard,
etc.) - Printers
- Webcams
- FireWire Devices
- Bluetooth Devices
- Serial Port
- Thunderbolt
- Network Share
- Thin Client Storage (RDP Storage)
- Infrared Dongle
Why Safetica

Easiest to Implement and Integrate
Safetica enables easy and swift deployment, seamlessly integrating into existing IT infrastructure to minimize compatibility issues. Enjoy enhanced data protection and
productivity without significant delays or disruptions.

Persistent Data Protection
Safetica’s persistent data classifications resist attempts to bypass DLP, even when files are archived, encrypted, or have a different extension. This protection extends to new documents and files leaving the protected endpoint.

Flexible Deployment Options
Safetica offers flexible deployment
options to businesses, with on-premise installation for maximum control and security, or cloud-based hosting for greater flexibility and scalability
Schedule a Demo
See how Safetica can disover, classify, and protect your most valuable data through a personalized demo.
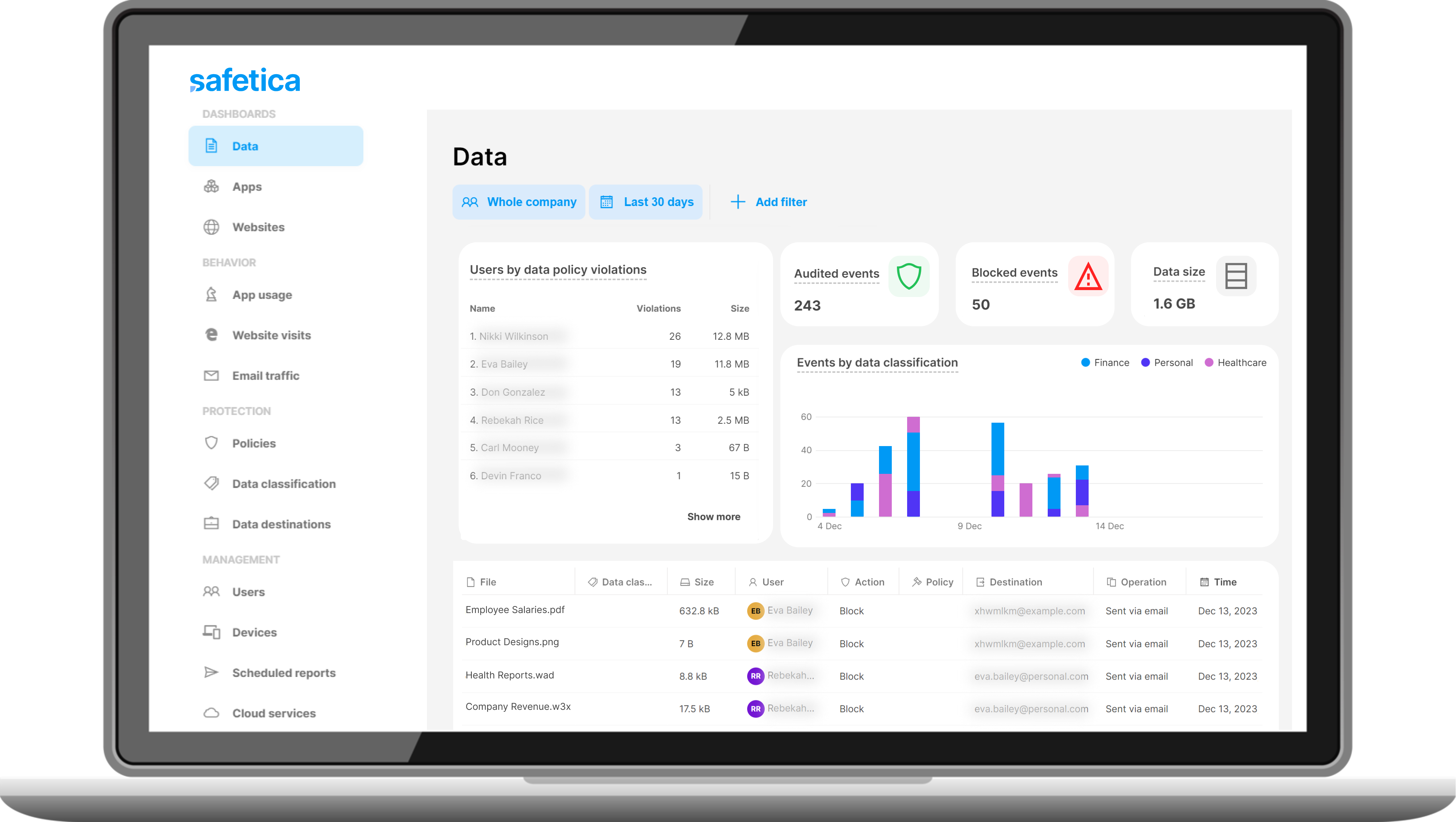
Explore Beyond Data Loss Prevention
Know what sensitive data you have and where it is with DATA DISCOVERY AND DATA CLASSIFICATION
Secure, manage, and monitor USB and peripheral port to protect data with DEVICE CONTROL
Proactively identify anomalous activities and detect insider threats with INSIDER RISK MANAGEMENT
Ensure compliance with data protection standards and avoid costly penalties with REGULATORY COMPLIANCE
Analyze risk in user activities and block dangerous actions with USER ACTIVITY AND WORKSPACE AUDIT
Users Love Safetica
Our customers appreciate our support, and find
Safetica easy-to-use, and fast-to-implement.






