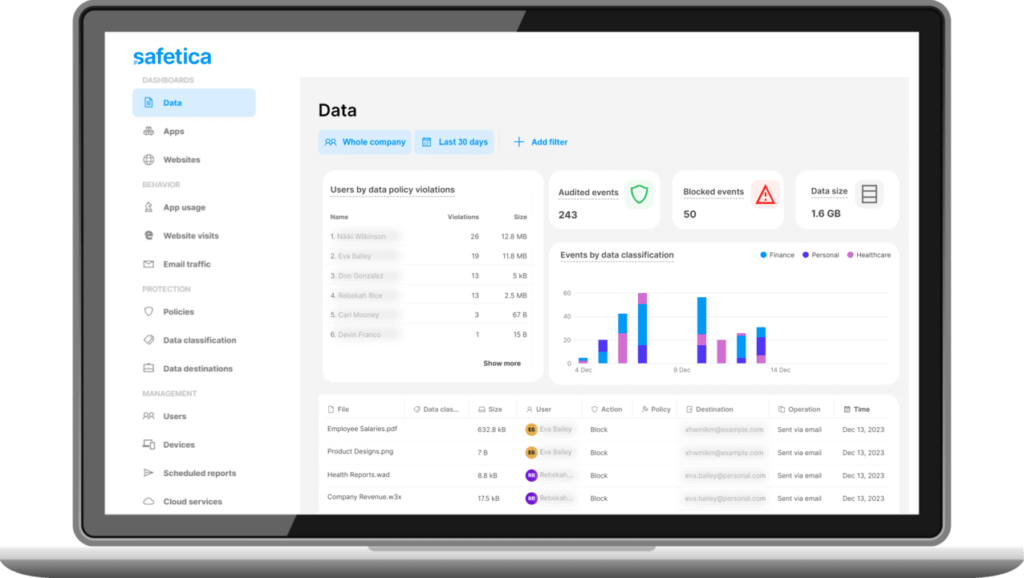
Data Discovery and Data Classification
Know what sensitive data you have, where it is, and how it’s used and take appropriate measures to keep it safe and secure.
Discover and Secure Sensitive Data
Data at rest
Safetica can search for sensitive files in selected folders on endpoints and in network shares.
Data in motion
Safetica can classify files directly during user operations, such as exports, uploads and downloads, opening files, copying files to a different path, uploading files via web browsers, sending files via email or IM apps, and others.

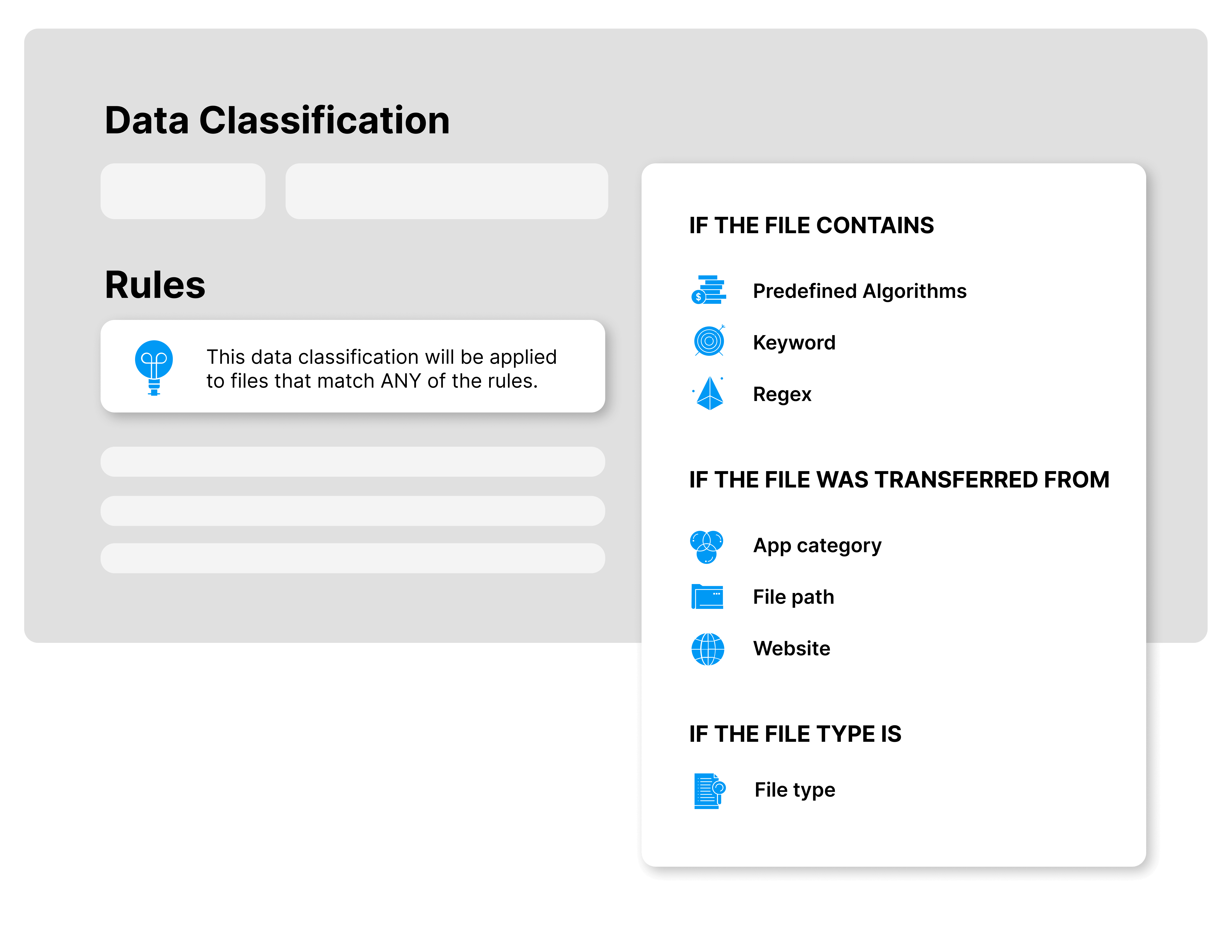
Streamline Your Data Classification with Safetica's Unified Approach
Safetica Unified Data Classification combines analyses of file content, file origin, and file properties, and ties into unified data protection policies.
For the user, this means that a single data classification can incorporate various types of rules and technologies. Powered by this unification approach, data policies can now apply to multiple data classifications and you no longer
need to create a special policy for each one of them. It’s that simple!
Content inspection
- Scanned PDF documents
- OCR
- Images with texts
- Built-in regional and industry
templates - Custom keyword dictionaries
- Regular expressions &
keywords
Context-aware Approach
- AutoCAD exports
- CRM exports
- Files stored on network file
share - Files stored on endpoints
- Files classified by users
Classification based on file properties
- AIP labels
- File attributes
- Spreadsheet files
Users Love Safetica
Our customers appreciate our support, and find
Safetica easy-to-use, and fast-to-implement.
Follow the 4 Steps to Data Security

Audit
Discover where your sensitive data is stored, transferred, or created. Monitor data transfers an user actions to detect any risky behavior that may lead to data loss.

Classify
Categorize sensitive data based on sensitivity and requirements. Assign labels (e.g., confidential, PII, IP to apply security controls, manage access, and ensure regulatory compliance.

Protect
Protect sensitive data with policies and rules. Enforce data handling guidelines and enable actions like blocking, quarantining, or alerting policy violations.
Report
Generate alerts, notify security teams, investigate incidents, and initiate response protocols to mitigate impact and prevent data loss or exposure.
Schedule a Demo
See how Safetica can disover, classify, and protect your most valuable data through a personalized demo.